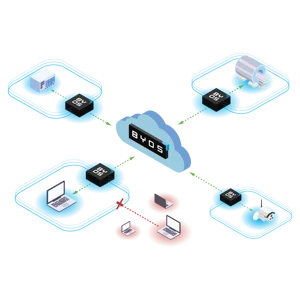
“I can’t connect my critical assets to the network because they would be exposed to attacks”
With Byos, devices can be invisible to the network they are connected to, while still being accessible from remote sources securely.
“My device has an unpatchable vulnerability and now I’m exposed”
Byos’ protection is decoupled from the device’s operating system, protecting the asset even if it presents OS-bound intrinsic vulnerabilities.
“I can’t provide remote access to critical resources securely”
Byos provides an invisible overlay network across multiple remote locations, allowing for secure remote access to assets without being conditioned by the local network the assets sit in.
Byos gives you an entirely new way to protect, control, and access your network
For Industrial IoT – Byos Brings Business Value
For Industrial IoT – Byos Brings Business Value
Quite simply – Business drivers are costing too much money.
Byos Brings:
![]() Secure Remote Troubleshooting, without exposing the network to the internet
Secure Remote Troubleshooting, without exposing the network to the internet
![]() A network for aggregation of data
A network for aggregation of data
![]() Prevention of the catastrophic risk of ransomware
Prevention of the catastrophic risk of ransomware
Invisible assets, full access, improved efficiency, and reduced costs. Immediate Time to Value.
For Industrial IoT – Byos Brings Business Value
You don’t have to choose between protected or accessible assets.
Byos Brings:
![]() Secure Remote IT Management
Secure Remote IT Management
![]() Secure Connectivity
Secure Connectivity
![]() Radically reduced attack surface
Radically reduced attack surface
Invisible assets, full access, improved efficiency, and reduced costs. Immediate Time to Value.
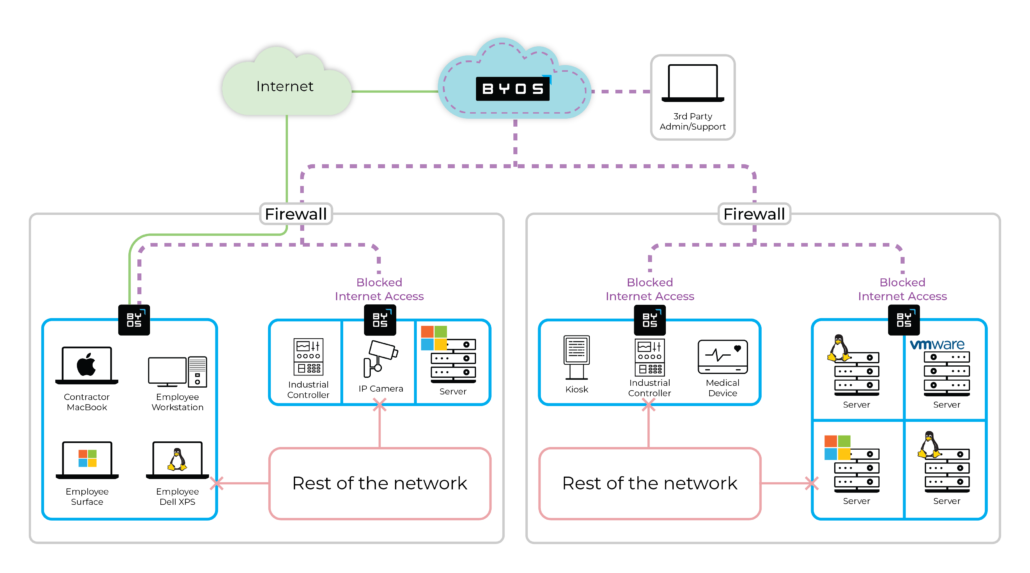
Byos allows you to control what your devices can and cannot do, even if those assets are in remote and uncontrolled locations.
Byos allows you to access any asset remotely, from and to uncontrolled networks, at the same time that those assets don’t have access to anything and at the same time that they are protected, and at the same time that they are invisible to the local network.
Before & After Byos
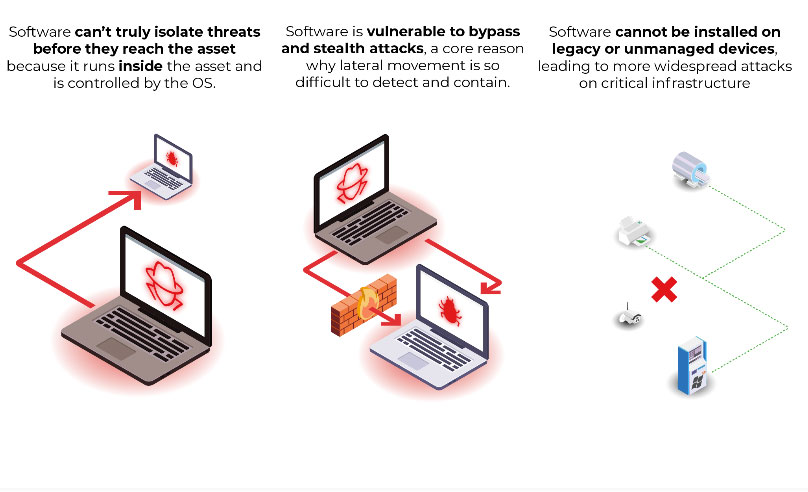
The most effective way to secure your network is to make every device undiscoverable and inaccessible
How Byos Transforms Security Operations
Simplify your stack
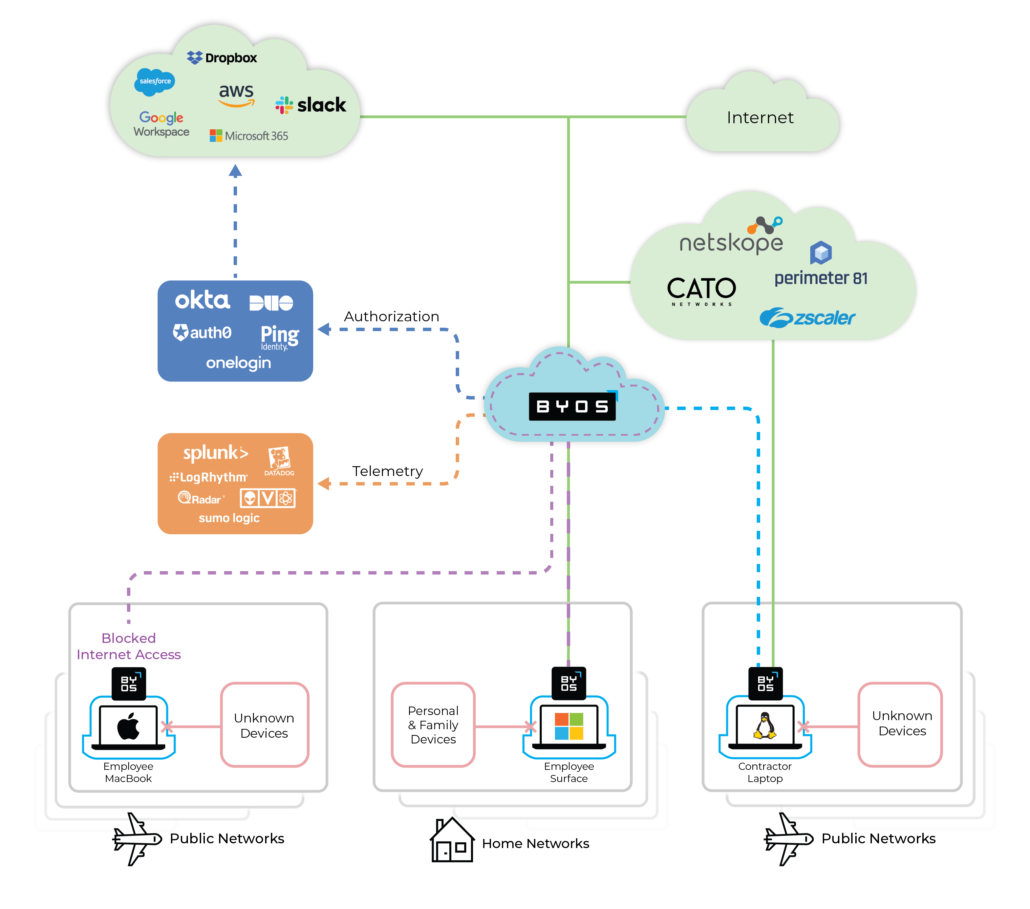
Accessing a given resource can be difficult because of the complexity involved in navigating a network with a disparate set of network and security technologies and policies. Byos delivers a streamlined path to a flatter, more consistent, and intuitive network design. It can be deployed in large, multinational organizations, regardless of network complexity or security technology.
Instant Visibility, Consistent Accessibility
You need centralized runtime visibility into the active sessions of distributed endpoints. Byos’ design drives consistency and simplicity across the enterprise. Customers tell us that the ease, simplicity and consistency in how they are are able to prepare and onboard new devices is worth paying for. And they just get the security for free. Can you set one policy for one of those devices, and then use the same access policy for each and every device in your network? With Byos, you can.
BYOS Products
Edge Security is Simple and Necessary
Byos Secure Endpoint Edge
There is a fundamental gap in protection between endpoints and the networks they connect to: endpoint and network security technologies fail to protect at the ingress/egress point of traffic to and from the endpoint, a.k.a. at the edge:
- Software-based endpoint protections installed on the OS can be bypassed/evaded.
- Perimeter-based protections cannot protect individual endpoints on the network before an attacker gains a foothold and propagates.
- Getting centralized runtime visibility into the active sessions of distributed endpoints is cumbersome with current tools.
Because of this, attackers leverage a number of tactics that many solutions are unable to protect against: Scanning/Enumerating/Fingerprinting, Eavesdropping, Remote Access Exploits, Evil-Twin Wi-Fi, Lateral Movement, and DNS hijacking to name a few.
The Byos Secure Gateway Edge
Byos’ Value Scope
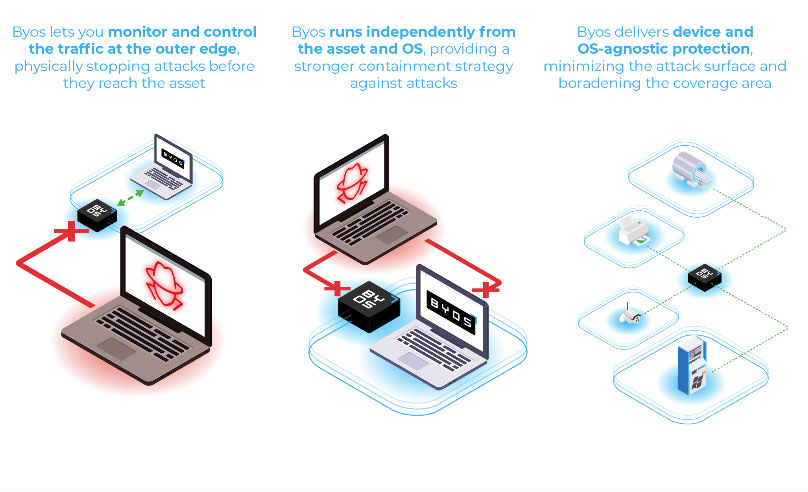
Invisibility
Byos makes devices invisible, and therefore physically unreachable by attackers on the network.
No lateral movement
With Byos, attackers that were able to gain access to the network won’t be able to move laterally across the network to attack other assets.
Asset decoupling
Byos doesn’t use an Agent, Driver, or Software running on the asset, therefore it is not governed by it. No asset compromise will turn into a Byos compromise.
No east/west traffic
Byos blocks all unprotected traffic between assets (typically called east-west traffic), and only allows communications through its Secure Overlay Network (north-south).
Secure remote access through distributed and uncontrolled networks
With Byos, assets are accessible via the Secure Overlay Network, regardless of their physical location.
Still Have Doubts? Don’t Take Our Word For It
Enterprise Design and Deployment in 3 Simple Steps
Step 1
Get Set Up Quickly in Just 2 Hours
Step 2
Give Us Your Toughest Challenges